While Investigating the Suspicious Traffic, it is important for an analyst to be clear what is really suspicious or not.
Below are few artifacts an analyst can observe to conclude if it is malicious or not.
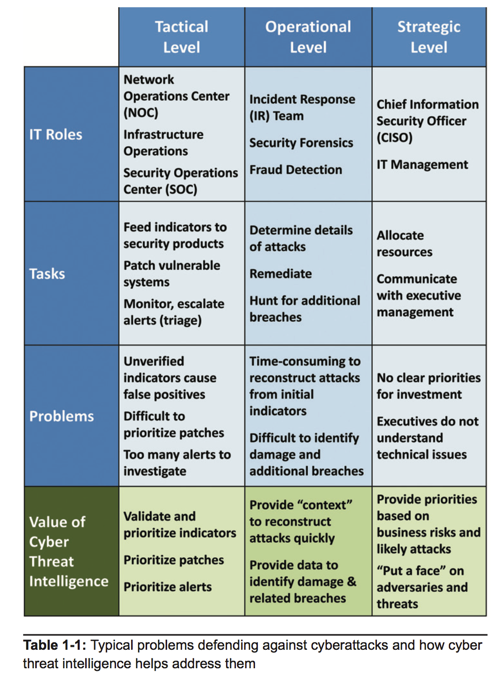
ARTIFACTS OF MALICIOUS IP
1) IP belong to High Risk Hosting Provider / Internet User IP
2) Has Malicious References on sites such as Sophos.com, mcafee.com,urlquery.net,snort.org,threatexpert.org,virustotal.com, malwr.org, xml.sandbox.net etc.,
ARTIFACTS OF MALICIOUS DOMAIN
If at least three of below criteria is matched, the domain would be malicious
1) Domain is NOT Popular
2) Has Malicious References on sites such as Sophos.com, mcafee.com,urlquery.net,snort.org,threatexpert.org,virustotal.com, malwr.org, xml.sandbox.net etc.,
3) Domain created date is less than 1 Year
4) Bluecoat Category is none / Suspicious / Malicious sources / Malicious Botnets / Dynamic DNS Hosts
5) No Site description
ARTIFACTS OF MALICIOUS WEB HEADER
1) User-Agent Field gives the idea what Is the application
Some malwares uses UA that appears legitimate, Hence check the UA used in other traffic for that IP at the same time
Some Malware uses exact UA that browser on infected machine uses, In that case check the header for other fields as described below to confirm if the web request is made by Browser/Malware.
2) Below fields in the Header indicate the request is made by a browser .
If they are not present, mostly the request is made by some malware/application
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
…
Cache-Control: max-stale=0
Pragma: no-cache
Connection: Keep-Alive
3) Referrer Field gives the Clue from where the user was redirected to
After confirming that Web Request is made by Browser,
If Referrer field is available,
a) If Referrer URL is yahoomail.com/live.com/gmail.com – indicating user infected from Phishing/SPAM
b) If Referrer URL is good blog/forum – indicating user infected from compromised site
If Referrer field is unavailable – User might have been Phished/SPAMed . (User clicking link from email in outlook)